
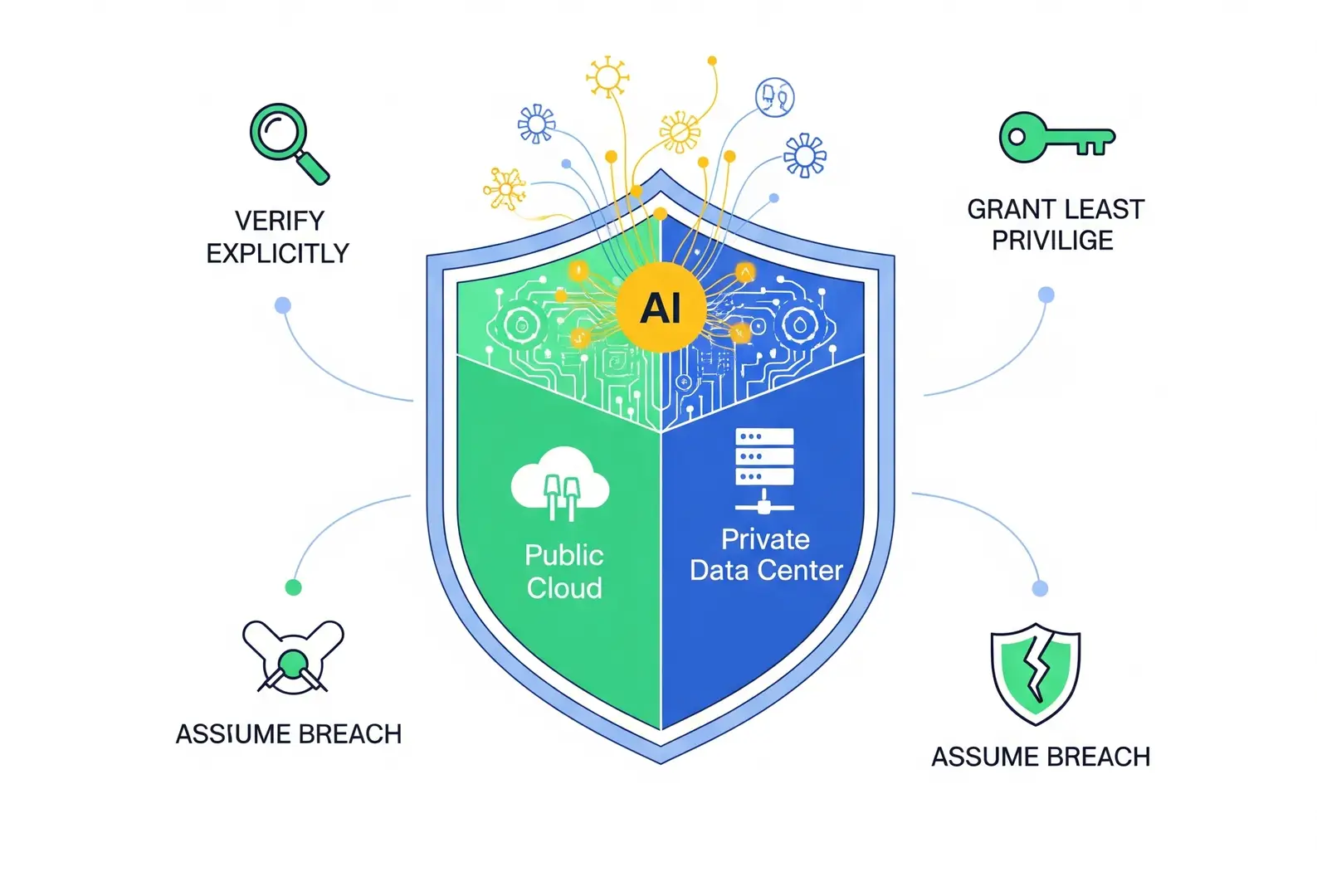
Why Enterprises Are Turning to AI-Powered Zero Trust for Hybrid Cloud Security
As businesses continue their digital transformation, there is a greater requirement than ever for strong and intelligent cybersecurity. Nowadays, a lot of businesses count on a combination of on-premises infrastructure and public & private cloud services.
This develops new risks even though it provides flexibility and scalability. Regular security models are no longer adequate. For this reason, more businesses are using AI-powered Zero Trust techniques to maintain the security of their hybrid cloud.
Hybrid Cloud and Its Security Challenges
Industry adoption of hybrid clouds has increased notably. It enables companies to take advantage of both public and private cloud platforms’ advantages. But that adaptability also brings complexity. IT teams must manage multiple systems, platforms, and users. This makes it harder to maintain visibility and control over cloud infrastructure security.
Cyber attackers are also becoming more advanced. They regularly take full advantage of identity and access errors rather than ignoring firewalls. Because of the rise in remote workers, third-party vendors, and cloud apps, traditional perimeter-based security is no longer effective. A new approach is required in recognition of the realisation that threats may appear from any point within the network.
What Is Zero Trust?
Zero Trust architecture is a security model that follows one simple rule i.e. never trust, always verify. Instead of assuming everything inside the network is safe, Zero Trust checks the identity and security posture of every user, device, & application. This is regardless where they are or what they are trying to access.
Key components of Zero Trust include:
- Identity and access management (IAM)
- Device verification
- Least-privilege access
- Real-time monitoring and analytics
This model is particularly effective in hybrid cloud environments, where there is no clear network perimeter to protect.
How AI Powers Zero Trust
While Zero Trust offers a strong security foundation, it can be complex to implement and manage at scale. That is where AI in cybersecurity comes in.
AI-powered Zero Trust solutions use artificial intelligence & machine learning services to automate many of the decisions and processes needed for Zero Trust.
Here’s how AI enhances Zero Trust:
- Analytics of user behaviour: AI looks for abnormalities by analysing patterns in user behaviour. The system has the ability to flag or block a user’s sudden access to sensitive data at an odd time.
- Automated threat detection: AI detects risk instantly, lowering down on response time and limiting harm.
- Modifiable enforcement of policies: AI simplifies the setup and management of access controls in large, dynamic environments, such as hybrid or multi-cloud infrastructures.
AI is being used by businesses to successfully put into effect Zero Trust, especially inside delicate cloud environments. AI enhances speed and accuracy while lessening the workload for human teams.
Advantages of Zero Trust Implementation in Cloud Environments
Given that remote and hybrid workers use network resources from multiple locations, an efficient security plan is crucial in a threat domain that is constantly changing. The proactive and extensive cybersecurity framework provided by zero trust can assist you in defending your cloud infrastructure and digital assets.
Here are some of the benefits of implementing a zero trust framework in modern cloud environments:
Data Breaches and Zero Trust
Incidents of data breaches have risen by 20% from year 2022 to year 2023, making them still one of the most major threats in the cyber world. In this current year, the number of individuals affected has grown noticeably more than it was in previous years. The concept called zero trust architecture can lessen risks from these breaches through safeguarding important information and enforcing robust authentication along with control over access. It also helps mitigate harm related to finance, law and reputation.
Improved Access Control
Zero Trust replaces traditional perimeter-based security with a model that treats all access requests as untrusted by default. It enforces least privilege access, requiring users and devices to verify their identity every time they connect.
Reduced Attack Surface
Attack surfaces have increased as a result of the move to cloud, edge computing, and remote work. Through micro-segmentation, Zero Trust lowers this risk by swiftly separating threats and preventing their spread.
Flexibility in Changing Situations
Zero Trust provides flexibility and scalability, making it ideal for dynamic cloud environments. Strong security is guaranteed by its adaptive authentication, even when workloads and cloud configurations change.
User and Device Authentication
Methods like MFA, OAuth, or OpenID Connect are employed for robust authentication which is an essential component of Zero Trust. These instruments ensure identities are real by using multiple steps such as passwords, biometrics, or tokens before allowing access.
Regulatory Alignment and Compliance
By putting in place access controls and constant surveillance, Zero Trust supports dedication to rules for data privacy. For example, the GDPR Article 32 demands that data must be encrypted which assists in safeguarding confidential information and ensuring only permitted users can reach it.
Final Thoughts
The shift to AI-powered Zero Trust is a crucial advancement in enterprise cybersecurity services. As hybrid cloud security is getting more complex, traditional tools and methods are no longer appropriate. AI gives Zero Trust the smartness, automatic functions and ability to expand that it needs to be useful and effective.
At present, businesses have the opportunity to enhance handling of identity and access, protect their cloud structure and remain active against new cyber dangers by using AI-powered Zero Trust. As digital ecosystems keep on growing, it will be essential to adopt this method for future-proofing security plans.
Related Posts
© 2026 Invastor. All Rights Reserved

User Comments